latest

How to install OTA updates and keep root on your Google Pixel phone
Looking for a way to keep root access after OTA updates on your Google Pixel phone? Here's a step-by-step guide on how to do so.
Part of the beauty of owning a Google Pixel phone comes through the proper availability of firmware images that can be used to return the device to a factory state. Even if you unlock the bootloader, root the phone, or tinker a bit too much, you can always restore the stock configuration. Having said that, some users might find it difficult to keep root access and associated mods intact while retaining the ability to take monthly security updates. Although many hardcore Android fans will know exactly what to do, not everyone is as adept at getting their phone updated without losing root.

Magisk's biggest update in months brings preliminary Android 14 support and other improvements
No more support for Android Lollipop, though
Magisk is probably a name that needs no introduction to Android modding enthusiasts, but for the uninitiated, it's a versatile open source software which allows for systemless root access. For the tinkerers and those still entrenched in the customizability of ROMs in the truest sense of the term, there are very few solutions that match Magisk and the vast array of Magisk modules. The tool is now being updated to version 26.0, which introduces support for the Samsung Galaxy S23 series as well as other Galaxy devices launched with Android 13 and lays the groundwork for Android 14.

Here's how to unlock the bootloader and root the Samsung Galaxy S23 right now
If you just got yourself a shiny new Galaxy S23, follow along this guide to root the phone with Magisk
Samsung's Galaxy S23 family represents the best that the Korean OEM has to offer this year. For the first time, all three devices in the lineup feature a custom flagship processor from Qualcomm across the globe, alongside the usual great camera hardware and stunning displays. There's also been a growing number of S23 fans brewing within the developer community since it was launched, which is evident from the rather swift TWRP release. If you have purchased one of the phones and have yet to root it with Magisk, here's a tutorial to guide you through the process.
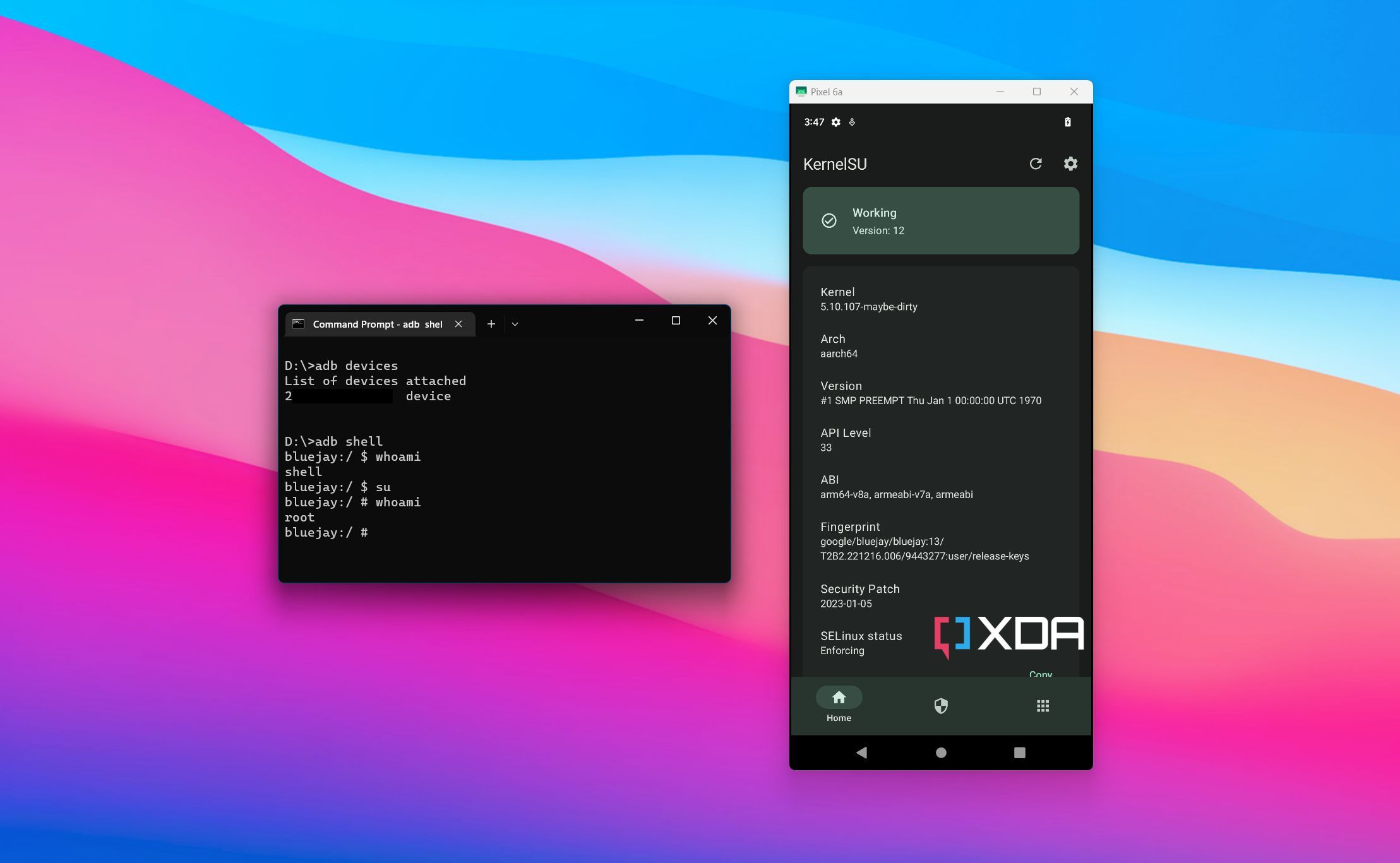
KernelSU reborn: Developer ports kernel-assisted root access to GKI compatible devices
A Magisk successor at last?
Among the Android modding circles, there's no app more recognizable than Magisk. It has a well-earned reputation as the de facto standard for rooting your phone, tablet, and really just about anything that runs Android. While Magisk managed to establish itself as the successor to Chainfire's SuperSU, the aftermarket development community stumbled on multiple root solutions during the transition phase. Apart from the notable ones, e.g. the LineageOS su add-on or XDA Recognized Developer phhusson's SuperUser, we also came across unique implementations, such as Kernel Assisted Superuser (KernelSU) by Jason Donenfeld AKA XDA Recognized Developer zx2c4.

Rooting Google Pixel 6 series requires help from the Pixel 7 on the latest Android 13 beta
Using the boot image from the Pixel 7 - yes, that's right!
As soon as Google kickstarted the beta initiative of Android 13's second Quarterly Platform Release (commonly referred to as QPR2), many enthusiasts expected that achieving root on these builds would be just as easy as rooting the stable channel firmware, but that didn't turn out to be the case. To be precise, the generic root guide that involves patching the boot image using Magisk stopped working for the Google Pixel 6 series. If you have a Pixel 6, 6 Pro, or Pixel 6a, neither the stable nor the Canary build of Magisk can generate a working patched boot image for superuser access on the QPR2 beta builds. But solving the riddle seemed to be a matter of when, not if, and the Android modding scene had already figured out a clever way to root the Pixel 6 lineup running Android 13 QPR2 beta by borrowing some bits from the Pixel 7.

Developers rooted the Spotify Car Thing, because why not
Security loopholes in the bootloader made it possible to bypass the chain of trust and gain root access
Spotify discontinued its 'Car Thing' accessory -- a touchscreen control panel for playing Spotify content in a car -- a few months ago. Even though the device got some additional features like hands-free calling before it was discontinued, the Car Thing won't be of much use in some time because the OS is far too limited. While we criticize such practices of planned obsolescence, praise must be lavished upon a group of developers who have now managed to root the Spotify Car Thing, opening up even more aftermarket development possibilities.

Here's how you can unlock the bootloader and root the Google Pixel 6a with Magisk
Looking to root your brand new Google Pixel 6a? Here's how to unlock the bootloader and root the latest mid-ranger Pixel smartphone!
It’s been a few weeks since Google unveiled the mid-ranger Pixel 6a, bringing several notable upgrades over previous Pixel-A series phones. Besides the availability of the Android 13 beta, the factory images and the kernel sources for the Pixel 6a have been published as well, which are just the right ingredients for the modding enthusiasts to start tinkering with the device.

Magisk v25.2 marks the beginning of the project's Rust-ification
The latest version of Magisk stable release (v25.2) comes with a plethora of bug fixes for MagiskInit and a Rust-powered logging interface.
Back in 2021, we saw the first baby steps toward the adoption of the memory-managed Rust programming language into the Android codebase. John Wu, aka XDA Senior Recognized Developer topjohnwu, has apparently been thinking along the same lines for the Magisk Project. As per Wu, the experimentation had already begun after releasing the v25.0 build of Magisk via stable channel. Now, topjohnwu has rolled out a new stable build of Magisk in the form of v25.2, with the whole logging infrastructure transitioned to Rust.

How to unlock the bootloader of the Nothing Phone 1 and root it with Magisk
Want to root your brand new Nothing Phone 1? Here's how to unlock the bootloader, flash a modified boot image, and install Magisk!
Upon the release of a new smartphone, a mission that many Android enthusiasts undertake is to unlock the bootloader and root the device. After this, typically comes a deluge of development in the form of custom ROMs, kernels, and other mods and tweaks. It can be said that the life of a device here at XDA doesn’t truly begin until the shackle (read "locked bootloader") has been thoroughly destroyed. For the Nothing Phone 1 community, that journey can start right now!
Researcher finds Android zero-day vulnerability impacting Google Pixel 6, Samsung Galaxy S22, and more
A security researcher has found a zero-day security vulnerability in Linux kernel that compromises the Google Pixel 6 and others phones.
Android security has come a long way in recent years. The fostering of monthly security patches has kept hundreds of threats at bay, while Google Play Protect is there to bar malware from the Play Store. However, there are still instances where rogue actors can exploit vulnerabilities hidden within in Android's code for nefarious purposes. Zhenpeng Lin, a security researcher and Northwestern University PhD student, recently discovered such a vulnerability on the Google Pixel 6, and you may be at risk even after installing the latest July 2022 security update.

How to unlock the T-Mobile LG Velvet bootloader and root it with Magisk
You can now unlock the bootloader of the T-Mobile variant of the LG Velvet and root it using Magisk. Read on to know how to do it!
Unlocking the bootloader, rooting a device, and flashing aftermarket ROMs are popular hobbies here at XDA. The power user community holds the ability to mod their devices in high regard, and they almost find no interest in phones if they are not able to be bootloader unlocked. Many legacy devices are actually kept alive by third-party ROMs, which are also godsends for smartphones that are standing on the verge of losing official support. LG, for example, no longer makes Android smartphones, hence owners of LG devices might want to settle with custom ROMs in the near future. However, the process isn't exactly straightforward due to LG's bootloader unlocking policy.

Magisk v25.0 improves SELinux handling, revises root permission management, and much more
The latest update for Magisk (v25.0) has been released with tons of bug fixes and feature improvements. Read on to know more!
At this point, we at XDA are certain that most of you have at least heard of Magisk. Created by John Wu, aka XDA Recognized Developer topjohnwu, the project originally started off as a systemless root method and has gradually evolved into a much more diverse and powerful solution beyond just a plain superuser privilege provider. It goes without saying that the developer and the contributors are always active and working hard to perfect it. The latest major update of Magisk, which corresponds to the twenty-fifth version (v25), has now arrived at the public beta branch. The changelog is subtle yet very important, so let’s dive into it.

PSA: Dirty Pipe, the Linux kernel root vulnerability, can be abused on the Samsung Galaxy S22 and Google Pixel 6 Pro
The infamous "Dirty Pipe" vulnerability can be exploited on the Samsung Galaxy S22 and the Google Pixel 6 Pro to gain root shell access.
What happens when a Linux privilege-escalation vulnerability that also affects Android gets disclosed publicly? You got it! Security researchers and Android enthusiasts around the world try to take advantage of the newly found problem to create an exploit, which can be used to gain advanced access to your device (such as root or the ability to flash custom images). On the other hand, device makers and a few determined third-party developers quickly take the responsibility to patch the backdoor as soon as possible.

Unofficial LineageOS 18.1 brings Android TV 11 to the third-gen Amazon Fire TV Stick lineup
You can now unlock the bootloader of your third-gen Amazon Fire TV Stick, flash a custom recovery, install Android TV 11 and much more!
When it comes to streaming dongles, Amazon Fire TV Sticks are some of the most popular streaming devices on the market. Amazon maintains its own fork of Android called Fire OS for these devices, which lacks Google apps and has a completely different UI than Google’s Android TV OS. If you own a 3rd generation Fire TV Stick or its Lite variant and aren’t satisfied with the out-of-the-box software experience, you can now swap the Amazon firmware for the source-built Android 11 ROM and enjoy the vanilla Android TV experience.

Linux kernel bug dubbed 'Dirty Pipe' can lead to root access, affects Android devices as well
Dirty Pipe is a newly discovered Linux flaw that can be exploited to gain root access. The bug also affects certain Android phones. Read on!
One of the strongest points of the Linux kernel has primarily been its open source nature, which allows stakeholders to fork, modify and redistribute it in a way that suits their particular needs. But this very advantage of being open source acts like a double-edged sword when it comes to the existence of unpatched security vulnerabilities and corresponding exploitable scenarios. While developers and big name OEMs are hard at work enhancing the overall security of the Linux ecosystem (which also includes Android), new vulnerabilities and exploits keep popping up and slipping under the radar. The mistake this time seems to be quite serious, unfortunately.

Magisk v24.2 released with Zygisk improvements, stability fixes, and much more
The latest public beta build of Magisk (v24.2) has been released with several bug fixes and Zygisk related improvements. Read on to know more!
As of 2022, Magisk is the most popular and recommended rooting solution for devices running Android. Created by John Wu, aka XDA Recognized Developer topjohnwu, the Magisk project has gradually evolved into a much more diverse and powerful tool beyond just plain root. A big part of its success comes from the developer’s consistency and dedication towards quality updates. The latest major version of Magisk, which corresponds to the twenty-fourth version (v24), was released back in January, featuring Zygisk and a plethora of interesting improvements. Now, topjohnwu has rolled out a new public beta build of Magisk in the form of v24.2, bringing several bug and stability fixes for root access.

Magisk v24.0 release introduces Zygisk, brings along Android 12 support, and more
The latest Magisk release now fully supports Android 12. It's also possible to run Magisk in the Zygote daemon process, thanks to Zygisk.
XDA Senior Recognized Developer topjohnwu's Magisk started off as a systemless root method and has evolved over the years into a much more diverse and powerful tool beyond just plain root. But even today, if you need root, chances are that the recommended root method for your device mentions installing Magisk for superuser access. The latest major update of Magisk, which corresponds to the twenty-fourth version (v24), has now arrived at the public beta branch, officially bringing full-blown support for all Android 12 devices wide and large.

You can now root your Oculus Go VR Headset, at least partially
You can now gain root access on the Oculus Go via Chainfire's SuperSU. This is helpful if you want to make system-level modifications.
Oculus -- a part of Facebook Meta makes some great VR headsets for gaming. The Oculus Go was a standalone VR headset from the company which was discontinued last year in favor of the Oculus Quest 2. If you're familiar with the way standalone VR headsets work, you would be aware of the fact that they run a version of Android. The Oculus Go also belongs to that category. Given that it runs a build of Android, there's now a way to (partially) root your Oculus Go.

OnePlus Nord 2 has a vulnerability that grants root shell access within minutes on a locked bootloader, without a data wipe
The OnePlus Nord 2 has a vulnerability that allows an attacker to get unrestricted root shell access. Read on to know more!
A lot of us here at XDA-Developers originally started browsing the forums for the first time when we were looking to root our Android devices. Back in those days, people often relied on "one-click root" methods: Apps or scripts containing payloads that target known privilege escalation vulnerabilities of the existing firmware to gain root access. With improvements and changes to encryption, permissions, and privacy-related handling, modern Android devices are relatively safe from such attack vectors, but there will always remain scope for exploits and vulnerabilities.
Should apps and games prevent users from customizing their smartphones?
Many Android apps and games block users for enabling developer options, rooting, or installing a custom ROM. Should they be allowed to do so?
One of the best things about Android is that it gives power users plenty of options to customize their devices. Users can easily root their phones to install custom ROMs and custom kernels, use powerful automation tools like Tasker, and do much more. However, rooting or modifying an Android phone does have a few downsides. For instance, some apps and games simply refuse to work on modded devices. This brings us to our discussion topic for today.



